Mobile phone usage is increasing, and according to research in 2020, the total number of unique smartphone users was 5.19 billion. Increasing mobile phone users have also led to higher application usage. Especially Android applications are pretty famous, with more than 70% market share. Such a broad reach can mean providing Android apps a secure experience becomes challenging.
Android apps are subject to many diverse types of cyberattacks like:
- Malicious code injections
- Dummy Apk’s
- App sandboxing
- Spyware
- Email and SMS spoofing
So, there is no denying that Android app security becomes key for enhanced user experience with several cyber threats. Securing your Android application is crucial for customers’ trust and better compliance. You need to follow several data regulation guidelines like HIPAA, GDPR, and PCI DSS for your applications.
The question popping in your head will be how to secure Android apps?
Well, the answers are right here; let’s discuss them!
Secure Application Code

Code injections are one of the most significant cyberattacks on Android applications. Take the example of Bosch. In January of 2022, the media outlet of Bosch Video Security systems released a statement indicating vulnerabilities in the Android apps.
According to the report, attackers could inject random HTML code into the WebView object. As a result, it can lead to malicious code injections and data theft. Similarly, your Android app is also prone to code injections, and that is why you need suitable security measures.
So, how do you avoid code injections?
There are several ways to improve Android app security against code injections like,
- Using a code signing certificate
- Input-output code sanitizations
- Data access authentications
Code Sign Your Android App

Code signing is a process that allows your application users to verify the source of the app. It enables validation of the app publisher and ensures that code integrity is intact. Code signing certificates are a sign of trust for your app users.
The code signing process uses a Public Key Infrastructure(PKI) technology to create digital signatures for your applications. The entire process depends on your private key and the contents of the program files.
Users receive a code signing certificate with the program file and public key bundled in a package. They use the certificate to verify the identity of the app publisher and the integrity of the code. For example, an app publisher uses the private key to raise a request for a code signing certificate to “Certificate Authority(CA).”
CA will validate the app publishers and assign a code signing certificate bundled with the public key. One of the critical aspects of a code signing certificate is hashing. It is a process that converts the code file into a random array of string values. Code files are first hashed and then code signed using the hashing algorithms.
I/O Sanitizations

Android apps deal with several third-party service integrations. This is why there are many avenues of malicious input or output. Here are some tips for sanitizing your code for higher Android app security,
- Disallow harmful content as input through filters
- Escape the bad content to make HTML text only
- Allow only safe HTML code
- Strip content of all HTML
- Replace the content with non-HTML tags and then filter out malicious HTML code.
Here you need to understand that a specific set of HTML tags are needed for different sanitization approaches. For example, if you are escaping the content, using < and > tags makes sense. This is because these tags allow the representation of the input as pure text rather than parsing of HTML, which is key to sanitization of malicious user inputs.
However, secure data access is one of the most significant ways to ensure a secure Android app experience.
Data Access Authentications

Securing the Android app by code sanitization is the post process. You can stop such malicious attacks in the initial stages through user authentications. It is a security measure to ensure that the data access is in the right hands. Modern apps do use methods like two-factor authentications to ensure security.
Two-factor authentication involves the user’s verifying their identity through an email address and username password with a second passcode. Then, an extra layer of authentication is added through the second passcode sent to the user’s device. While it is a practical approach, Android developers can use a modernized method by integrating fingerprint scanning.
So, users can use the fingerprint scanning feature of the smartphone for that extra layer of authentication rather than a passcode. Fingerprint scanning benefits include higher Android app security and a risk-free experience.
Another approach is to provide one-time access to data for your users through FLAG_GRANT_READ_URI_PERMISSION and FLAG_GRANT_WRITE_URI_PERMISSION flags. It will allow you to restrict data access and ensure an Android app secure experience.
These are your code security methods, but what if a user chooses an external app to share sensitive information? The answer is an app chooser.
App Chooser

Google recommends app developers to use an app chooser for users to share personal information only through trusted apps. It forces them to choose from specific app options that you provide, and which are trustworthy.
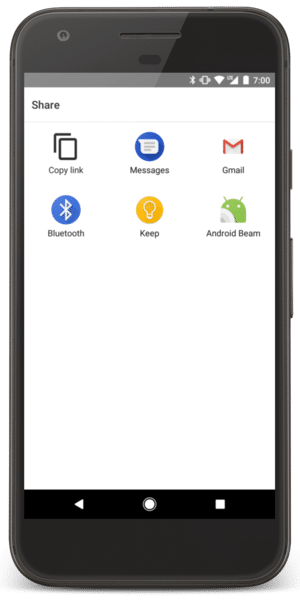
As you can see in the above image, you can use the app chooser and show specific apps to users for selection. Here is a Java-based code that you can use to show a chooser dialog:
Intent intent = new Intent(Intent.ACTION_SEND);
List<ResolveInfo> possibleActivitiesList = getPackageManager()
.queryIntentActivities(intent, PackageManager.MATCH_ALL);
// Verify that activity in at least two apps on the user's device can handle the intent.
// Otherwise, start the intent only if an app on the user's device can handle the intent.
if (possibleActivitiesList.size() > 1) {
// Create intent to show chooser.
// Title is something similar to "Share this photo with."
String title = getResources().getString(R.string.chooser_title);
Intent chooser = Intent.createChooser(intent, title);
startActivity(chooser);
} else if (intent.resolveActivity(getPackageManager()) != null) {
startActivity(intent);
}
Once you apply the code, an app chooser will be shown to the user each time they choose to share or provide information to external apps.
Conclusion
Providing a secure Android app experience can be challenging without a security strategy. Unfortunately, there is no silver bullet solution to secure Android apps. However, if you analyze your application security needs, assess all the approaches we discussed, and compare, a clearer picture will emerge. So, start securing your apps for an enhanced user experience.






![WI-FI Names [Cool & Funny]](https://cdn.xtechkr.com/wp-content/uploads/Best-Wi-Fi-Names-Collection-Featured-100x100.png)
